Intelligent Operations Playbook for Wealth Management Firms Formerly Bleakley Financial, OnePoint needed to eliminate manual data extraction between Orion portfolio management and Read More
Dreamforce Decoded For Marketing Leaders We’ve moved to the cloud, mobile, social and predictive AI. Now, we enter a new era – Read More
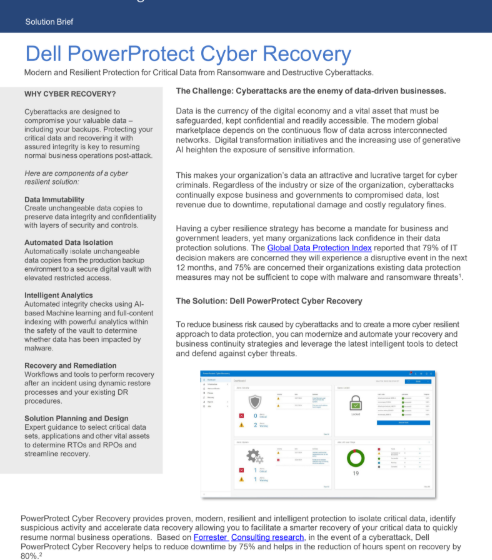
Dell PowerProtect Cyber Recovery Data is the currency of the digital economy and a vital asset that must be safeguarded, kept confidential Read More
Choosing the right PEO: The easy way to decide Partnering with a PEO can be a game changer, providing your company with Read More
A Buyers Checklist: How to Compare Professional Employer Organizations Choosing a professional employer organization (PEO) to do business with isn’t a Read More
Data Science vs. Machine Learning: What’s the Difference? With the recent explosive growth of artificial intelligence, two connected fields are seeing Read More
A Guide to the Key Stages of AIOps AIOps can increase the efficiency of IT workflows. Because AIOps encompasses a variety of Read More
MIT SMR CONNECTIONS Heimes: Every organization, from the smallest business to the largest corporation, has some form of procurement function. They need Read More
Bericht zum Stand der Beschaffung 2025 Heute spielt die Beschaffung eine strategische Rolle bei der Förderung von Innovationen, der Steigerung der betrieblichen Read More
Effective onboarding and mentorship in SOC teams In a security operations center (SOC), people are the most critical asset. Advanced tools and Read More